Streamline Your IT Infrastructure with Managed Data Protection Services
Streamline Your IT Infrastructure with Managed Data Protection Services
Blog Article
Just How Managed Data Defense Safeguards Your Company From Cyber Dangers
In a period where cyber risks are increasingly sophisticated, the value of handled data defense can not be overemphasized. Organizations that apply detailed protection procedures-- such as information file encryption, gain access to controls, and continuous surveillance-- are much better outfitted to guard their delicate details.

Comprehending Managed Data Protection
Managed information security is a crucial element of modern cybersecurity approaches, with approximately 60% of companies going with such services to guard their crucial details assets. This strategy entails outsourcing information protection duties to customized solution providers, permitting companies to concentrate on their core company functions while ensuring durable safety and security steps remain in location.
The significance of taken care of data protection hinges on its ability to offer detailed remedies that consist of information back-up, healing, and hazard detection. By leveraging innovative technologies and experience, managed provider (MSPs) can apply aggressive actions that mitigate threats connected with information breaches, ransomware attacks, and various other cyber threats. Such solutions are made to be scalable, suiting the progressing requirements of businesses as they grow and adjust to brand-new obstacles.
Moreover, took care of data protection assists in compliance with regulative needs, as MSPs often remain abreast of the current sector criteria and methods (Managed Data Protection). This not just boosts the safety and security posture of an organization but additionally instills confidence amongst stakeholders relating to the stability and discretion of their data. Ultimately, understanding taken care of data defense is critical for organizations seeking to strengthen their defenses versus the ever-changing landscape of cyber dangers
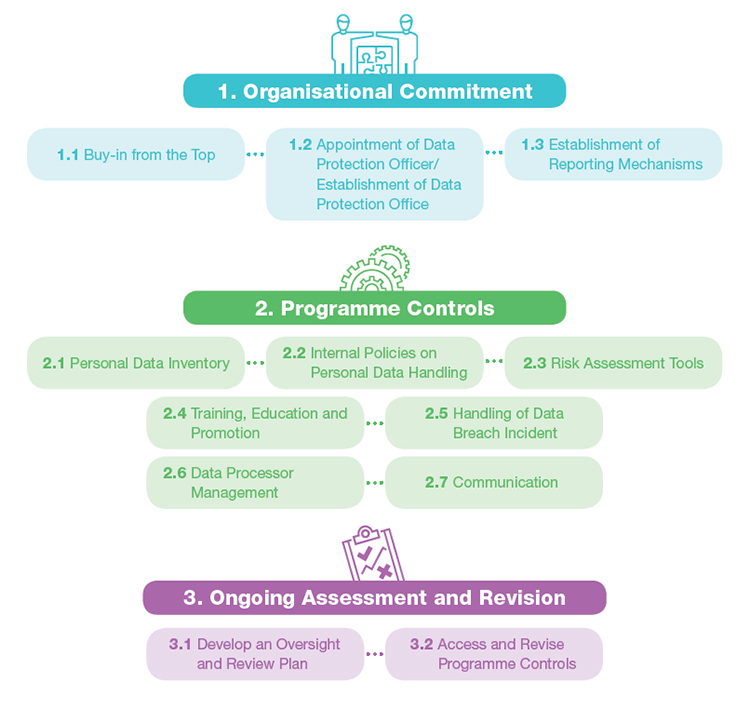
Trick Parts of Information Defense
Efficient data defense approaches usually incorporate numerous essential elements that operate in tandem to protect delicate information. Data security is crucial; it changes readable information into an unreadable format, ensuring that even if unapproved access happens, the details continues to be protected.
Gain access to control is one more critical element, allowing companies to restrict information accessibility to licensed employees only. This reduces the threat of internal violations and improves liability. Regular data back-ups are crucial to guarantee that info can be brought back in the event of information loss or corruption, whether due to cyberattacks or unintentional removal.
Following, a durable security policy need to be established to describe treatments for data taking care of, storage space, and sharing. This policy needs to be consistently upgraded to adapt to evolving risks. In addition, continuous surveillance and auditing of data systems can detect abnormalities and possible breaches in real-time, helping with speedy reactions to threats.
Benefits of Managed Services
Additionally, took care of services promote aggressive monitoring and danger discovery. MSPs make use of innovative modern technologies and devices to continuously monitor systems, making certain that anomalies are recognized and dealt with before they intensify into serious concerns. This proactive method not just reduces response times but additionally minimizes the prospective impact of cyber events.
Cost-effectiveness is one more essential benefit. By contracting out information defense to an MSP, organizations can stay clear of the considerable expenses related to in-house staffing, training, and modern technology investments. This allows business to allot resources much more effectively while still gaining from top-tier safety and security services.
Compliance and Regulatory Assurance
Ensuring conformity with industry regulations and criteria is a vital aspect of data protection that organizations can not neglect. Regulatory structures, such as GDPR, HIPAA, and PCI DSS, enforce learn the facts here now strict demands on how services handle and shield sensitive information. Non-compliance can result in severe penalties, reputational damage, and loss of client trust fund.
Managed information defense solutions assist organizations navigate the facility landscape of compliance by executing durable safety measures customized to meet details governing needs. These services offer systematic strategies to data encryption, gain access to controls, and regular audits, ensuring that all protocols align with legal obligations. By leveraging these taken care of services, businesses can keep continuous oversight of their data security techniques, making sure that they adapt to progressing laws.
Additionally, thorough reporting and paperwork supplied by managed information security services work as valuable devices throughout conformity audits. These records demonstrate adherence to established procedures and criteria, offering assurance to stakeholders and regulative bodies. Eventually, investing in managed information defense not only strengthens a company's cybersecurity position yet additionally imparts self-confidence click now that it is committed to maintaining compliance and regulatory assurance in a significantly complex electronic landscape.
Selecting the Right Provider
Picking the ideal managed information security provider is essential for companies intending to boost their cybersecurity structures. The initial step in this process is to review the supplier's know-how and experience in the area of information protection. Search for a copyright with a proven performance history of successfully guarding services versus numerous cyber dangers, as well as knowledge with industry-specific guidelines and conformity requirements.
In addition, evaluate the variety of solutions supplied. A detailed copyright will supply not only back-up and healing remedies yet also proactive hazard discovery, danger evaluation, and event feedback abilities. It is important to ensure that the provider uses sophisticated modern technologies, consisting of security and multi-factor verification, to safeguard sensitive information.
A responsive assistance group can considerably impact your organization's capability to recoup from events swiftly. By meticulously analyzing these elements, companies can make an informed decision and pick a company that straightens with their cybersecurity objectives, ultimately reinforcing their defense against cyber hazards.
Conclusion
In conclusion, handled information defense acts as a vital protection against cyber risks by employing durable safety actions, specific know-how, and advanced technologies. The combination of extensive strategies such as data encryption, access controls, and constant surveillance not only reduces threats yet likewise ensures conformity with governing standards. By outsourcing these services, companies can boost their protection structures, helping with quick recovery from data loss and fostering confidence amongst stakeholders despite ever-evolving cyber hazards.
In an era where cyber dangers are significantly innovative, the significance of taken care of information security can not be overemphasized.The essence of taken care of data defense exists in its ability to provide comprehensive services that include information back-up, recuperation, and danger discovery. Inevitably, understanding handled data security is critical for organizations looking for to fortify their defenses versus the ever-changing landscape of cyber threats.
In verdict, handled information security serves as an essential defense versus cyber threats by employing robust security measures, specific proficiency, and progressed innovations. Managed Data Protection.
Report this page